This week, the Apache Software Foundation has made an announcement that revealing a major security vulnerability/exploit where servers running in Apache HTTP Server 2.4 releases 2.4.17 to 2.4.38.

According to the Apache team, the vulnerability, tracked as CVE-2019-0211, affects Apache web server releases for Unix systems only, from 2.4.17 to 2.4.38, and was fixed this week with the release of version 2.4.39. The non-Unix systems and LiteSpeed Web Server are not affected.
Along with this major flaw, two other control bypass security vulnerabilities and three less severe flaws which potentially could have led to normalization inconsistency issues and crashes were also patched with the Apache HTTP Server 2.4.39 release.
More Details:
https://httpd.apache.org/security/vulnerabilities_24.html
According to an analysis conducted by Rapid7 Labs, more than 2,000,000 servers, many on public cloud platforms, are still running vulnerable versions of Apache. Most of the flawed systems are in the United States (~770,000), Germany (~224,000), and France (~111,000).
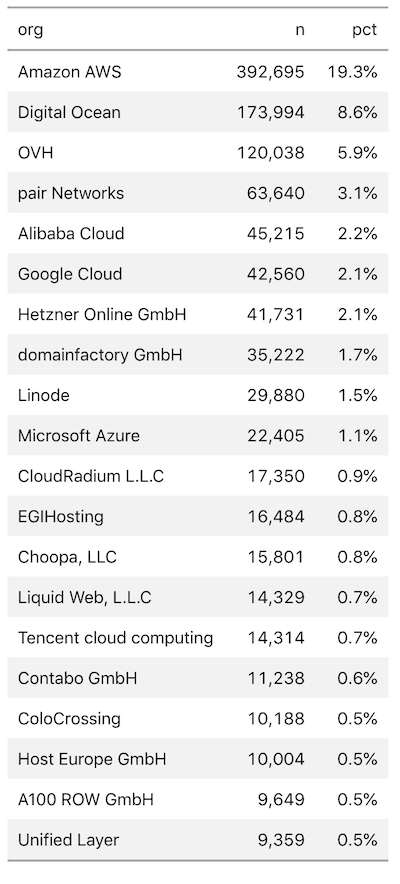
As you can see, there are many servers of Amazon AWS, DigitalOcean, OVH and others are affected by this serious security error. So if your server using these versions of Apache, we did recommend updating as soon as possible. System administrators can run the following command lines to update your Apache server to the latest 2.4.39 version.
CentOS based server
Ubuntu 18.04, Ubuntu 16.04
Keep monitoring on Ubuntu CVE Tracker and update your system as soon as the OS vendor publishes vulnerability fix.
Debian 9
According to Debian CVE-2019-0211 security tracker the vulnerability has been fixed in Apache 2.4.25-3+deb9u7. Run following command line to update your server and fix the issue.
All servers using cPanal/WHM have been automatically upgraded. But you can do this manually by running:
After update the Apache version, let recheck to ensure your current Apache version is 2.4.39 or higher, use the following command:
Hope this help!



